In the rapidly changing world of cloud computing, AWS IAM plays a critical role in making sure that only the right people have secure access. IAM, which stands for Identity and Access Management, gives users the power to control who can do what, ensuring that only the necessary permissions are given out. It's more than just confirming who you are – IAM also provides a strong way to safely share and work together across different accounts. At its core, IAM policies are really important because they define what actions are allowed, making sure everything stays secure. In this blog, you will learn more about the significance of AWS IAM and how it contributes to maintaining robust cloud security.
Now, Let's Get Into the Story :

Real-Life Example:
imagine you have a big box of toys, and you want to share some of them with your friends, but you also want to make sure that only your closest friends can play with certain toys. This is where AWS IAM comes in, and it's like having a special helper to manage who can play with which toys.
So, let's say you have three friends: Timmy, Sarah, and Alex. Timmy is your best friend, so you want to let him play with all the toys. Sarah is a good friend, but not as close as Timmy, so you only want her to play with the cars and trucks. Alex is a new friend, and you're not sure yet, so you don't want him to play with any toys for now.
Connecting the Story to IAM Service:

In AWS IAM terms:
Timmy is like the "Administrator" who can play with all the toys.
Sarah is like a "User" who can only play with the cars and trucks.
Alex is like a "Guest" who can't play with any toys yet.
Understanding IAM's Building Blocks:
1) Users:
Imagine making a new person part of the security plan. It's like giving them a badge that lets them into a building. When someone joins a company, they get a special 'badge,' which is like a user profile. This profile lets them use cloud services in AWS. But it's not just about getting in – it's about saying what they're allowed to do once they're in. This is where policies come in.
2) Policies:
Policies are like rules that say what a person can do in the cloud. These rules decide what they can change, see, or use. Without policies, someone might get in but not be able to do much. Policies make sure people have the right permissions to do their jobs well. It's like giving someone keys to some rooms, but only letting them open certain doors.
3) Groups:
Imagine lots of people coming and going. Setting up access for every person can be a hassle, right? That's where groups come in. Think of groups as categories that help manage access. As a DevOps engineer, you can group people as 'developers,' 'QA engineers,' 'DB administrators,' and more. Instead of giving each person access one by one, you give access to groups. So, when a new person joins, you just put them in the right group – it's like giving them a membership card.
4) Roles:
Roles work a bit differently. Imagine an app needing access to a cloud service. It's not a person, but it still needs to get in. Roles act like temporary passes for this. For example, if an app needs data from a cloud database, you create a 'role' for it. This role lets the app in for a short time and specific tasks. It's like lending your friend your Netflix account for a movie night – you trust them, but you set limits.
By understanding these basic ideas, you'll be better at using AWS IAM and making your cloud setup more secure and smooth.
Let's Do a Hands-on :
Exercise :
As you probably know at this point, it's not recommended to work with the root account in AWS. For this reason, you are going to create a new account that you'll use regularly as the admin account.
Create a user with password credentials
Add the newly created user to a group called "admin" and attach to it the policy called "Administrator Access"
Make sure the user has a tag called the key
Roleand the valueDevOps
Solution :
Go to the AWS IAM service

Click on "Users" in the right side menu (right under "Access Management")
Click on the button "Add users"

- Insert the user name (e.g. Kelvin)

Select the credential type: "Password"
Set the console password to custom and click on "Next"
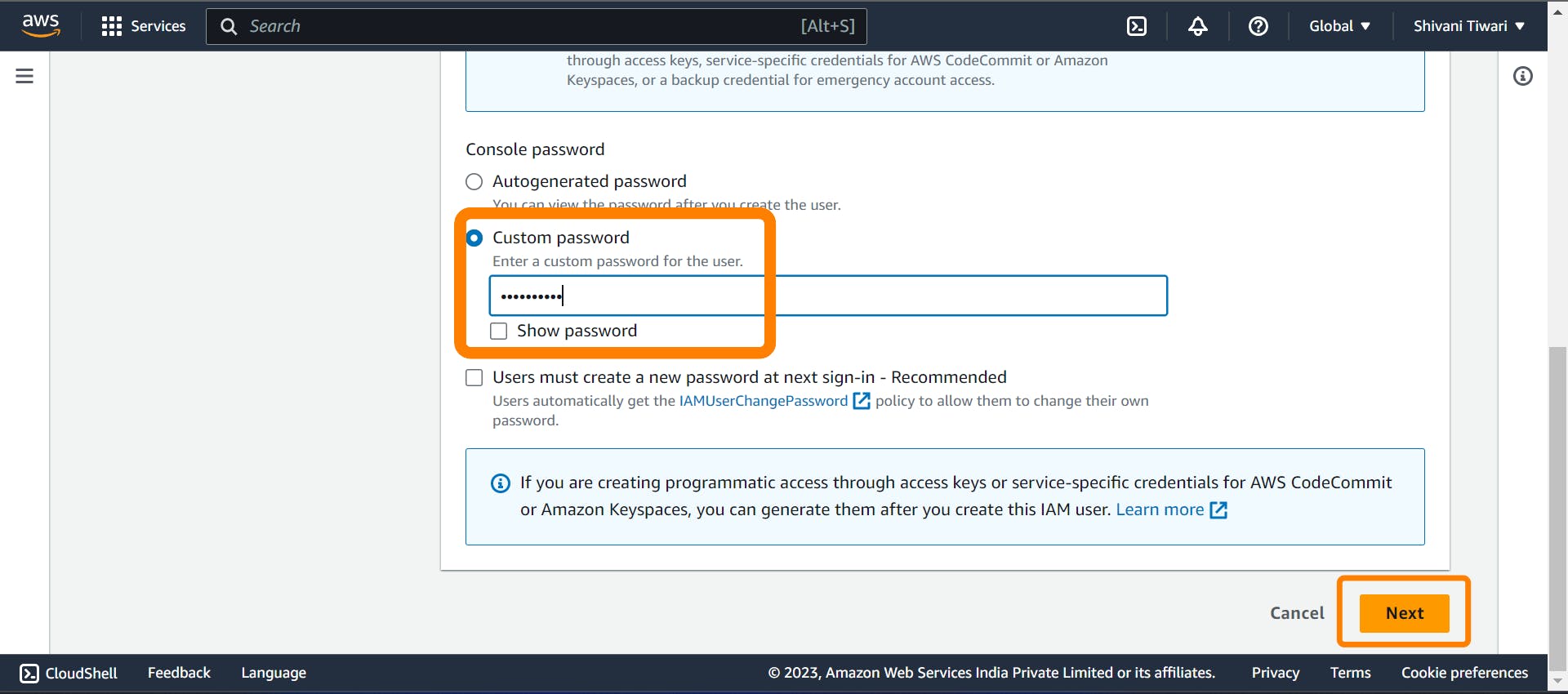
- Click on "Add user to group"
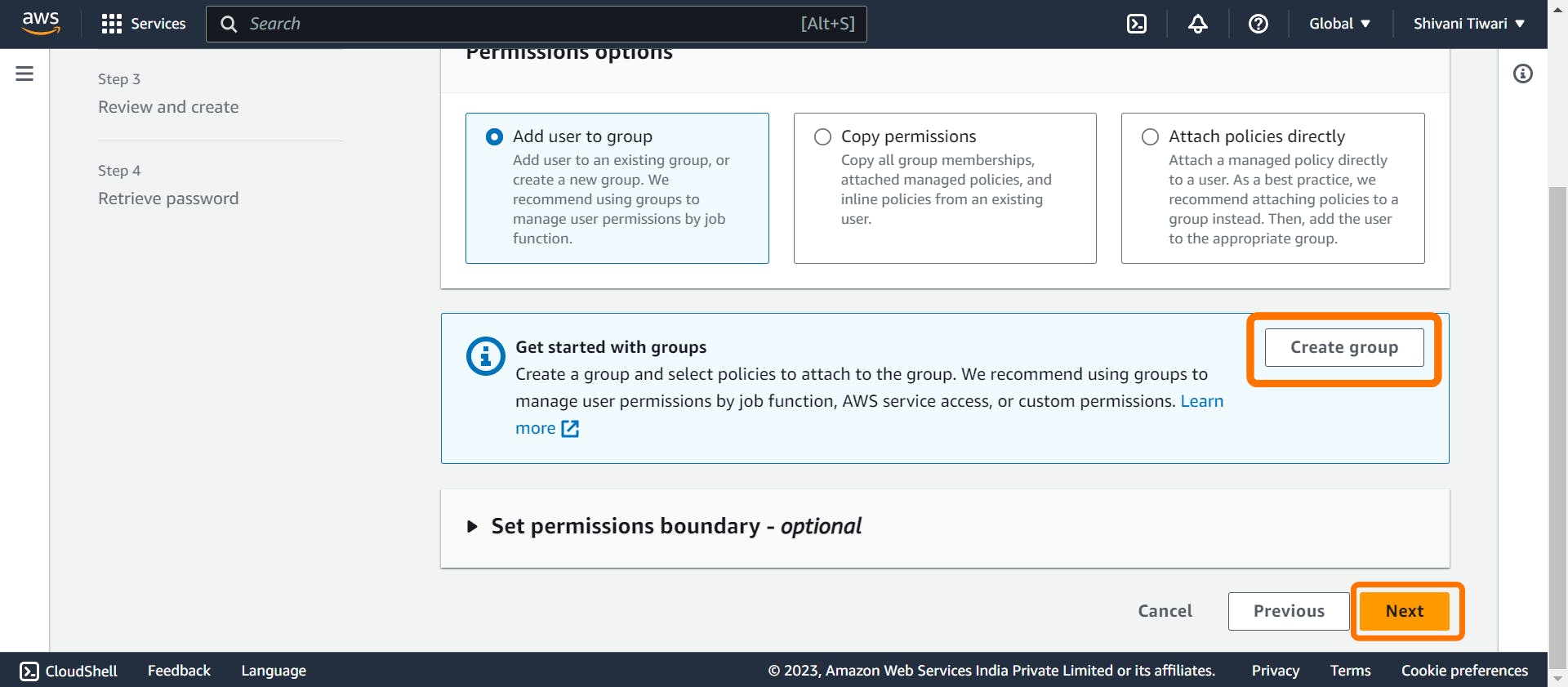
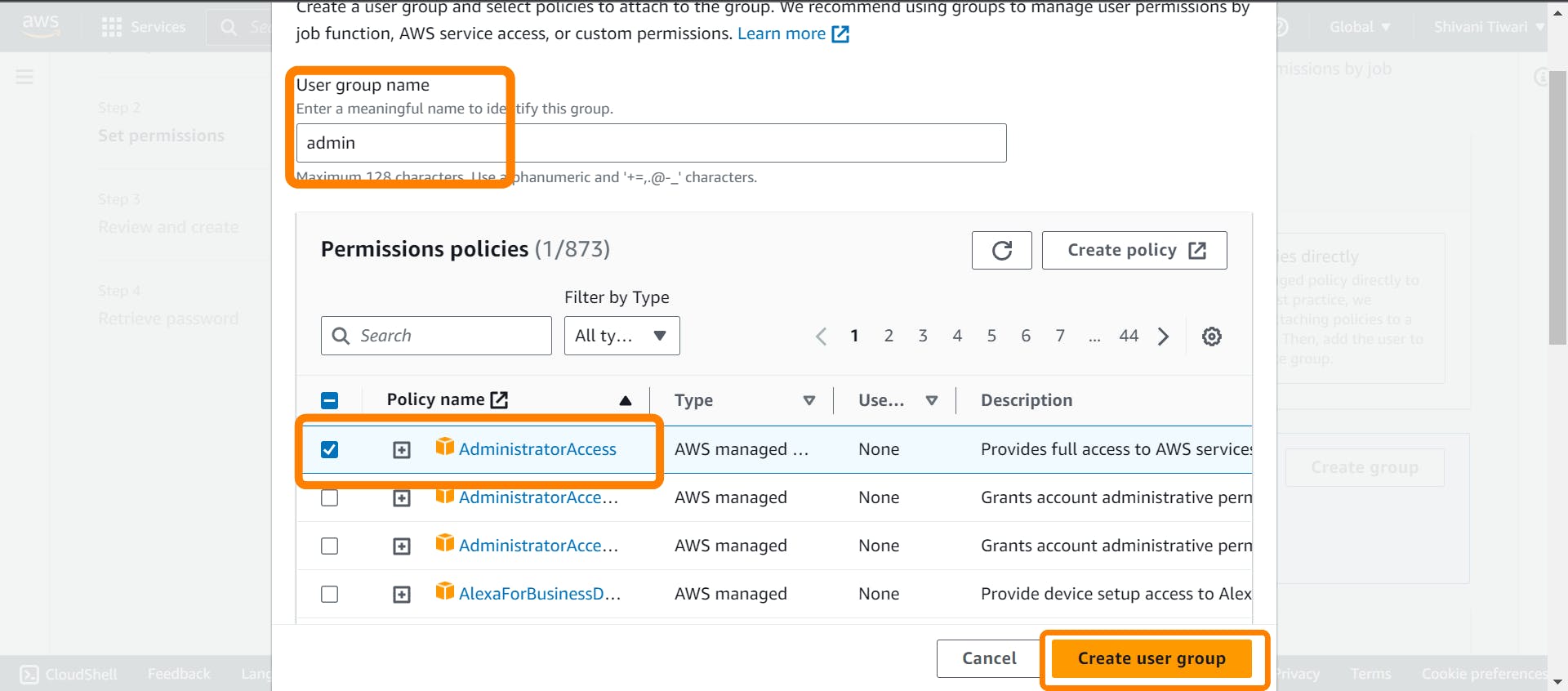
Insert "admin" as the group name
Check the "Administrator Access" policy and click on "Create group"
Click on "Next: Tags"
- Add a tag with the key
Roleand the valueDevOps
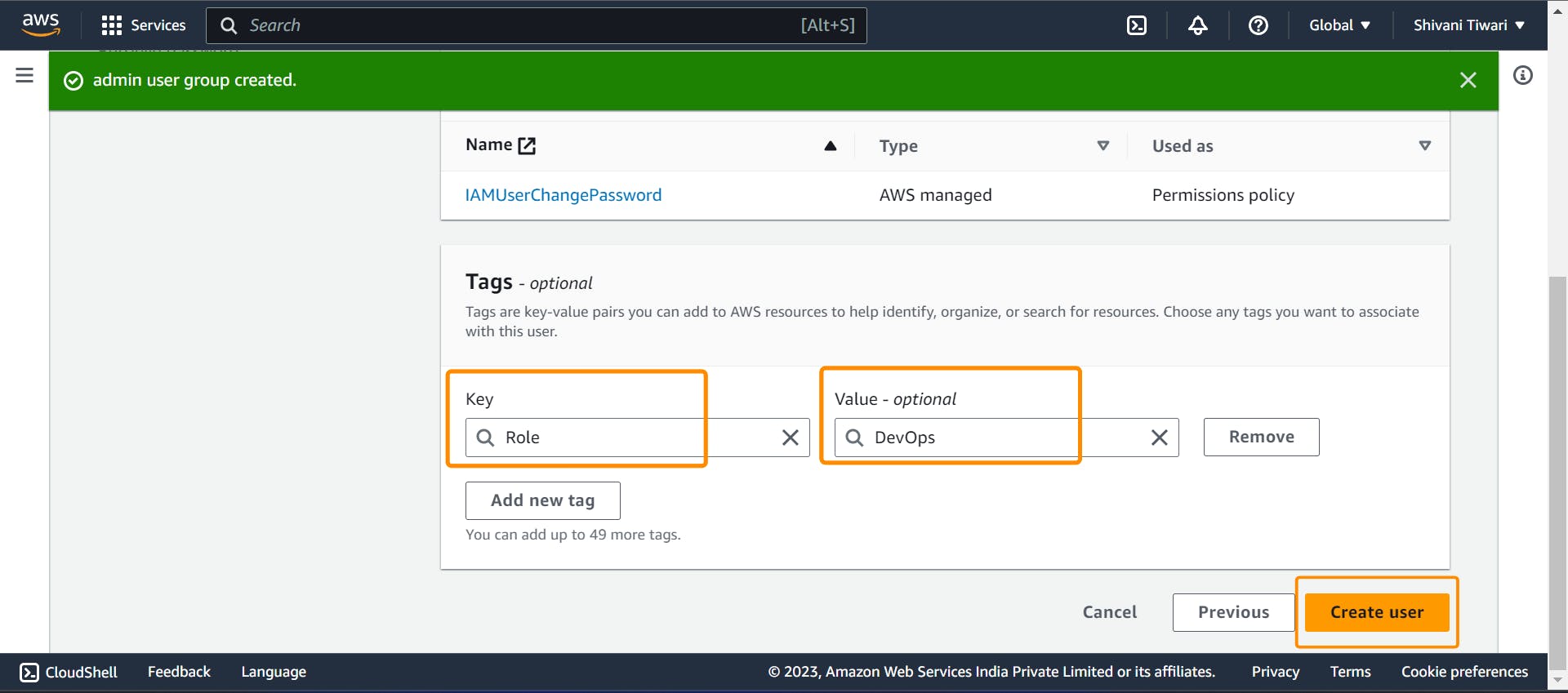
- then create on "Create user"

Conclusion :
To sum up, AWS Identity and Access Management (IAM) is like a guard for cloud setups. It uses users, policies, groups, and roles to make sure access is secure. Just like the bank controls who goes where, IAM gives out special keys, stopping chaos and problems. Policies shape access, groups manage users, and roles add security – all similar to controlled lending. Knowing these ideas helps you use AWS IAM better, making your cloud secure and efficient. The exercise shows how important IAM is by helping you create users and give them permissions, showing how to use IAM in real situations for better cloud security.
